Ugh I want a pedicure now. Anywho, I’m not going to delve deep into T1 Circuits, ISPS, WAN Communication, and other explanations about how wireless signals communicate. Rather, I figured I’d just let you in on a few small WiFi Attacks that have existed in the past, present, and future. Have a home security system on the internet? Use Snapchat or TikTok daily? I know you’re on Instagram. Enjoy yourself, but do ensure you are protected while you scroll. Let’s get started.
Have you ever heard of the legacy attack ‘War Dialing?’ It’s pretty straightforward, all of the numbers in a prefix are dialed in your area code, which results in a number of active computer modems. The act of War Driving is very similar. War Driving is an attack where a person seeks to find WiFi Networks that they are not permitted to access. Once the Hacker finds your WiFi network, he/she will verify whether or not you’re using Encryption, the Encryption Type, and whether or not it can be compromised. Once said Hacker has made that determination, he/she uses cracking tools to force an entry into the connection to conduct MITM attacks. Watch my Webinar to learn exactly how these Hackers (who drive around in vans all day looking for your WiFi signals…) HACK.
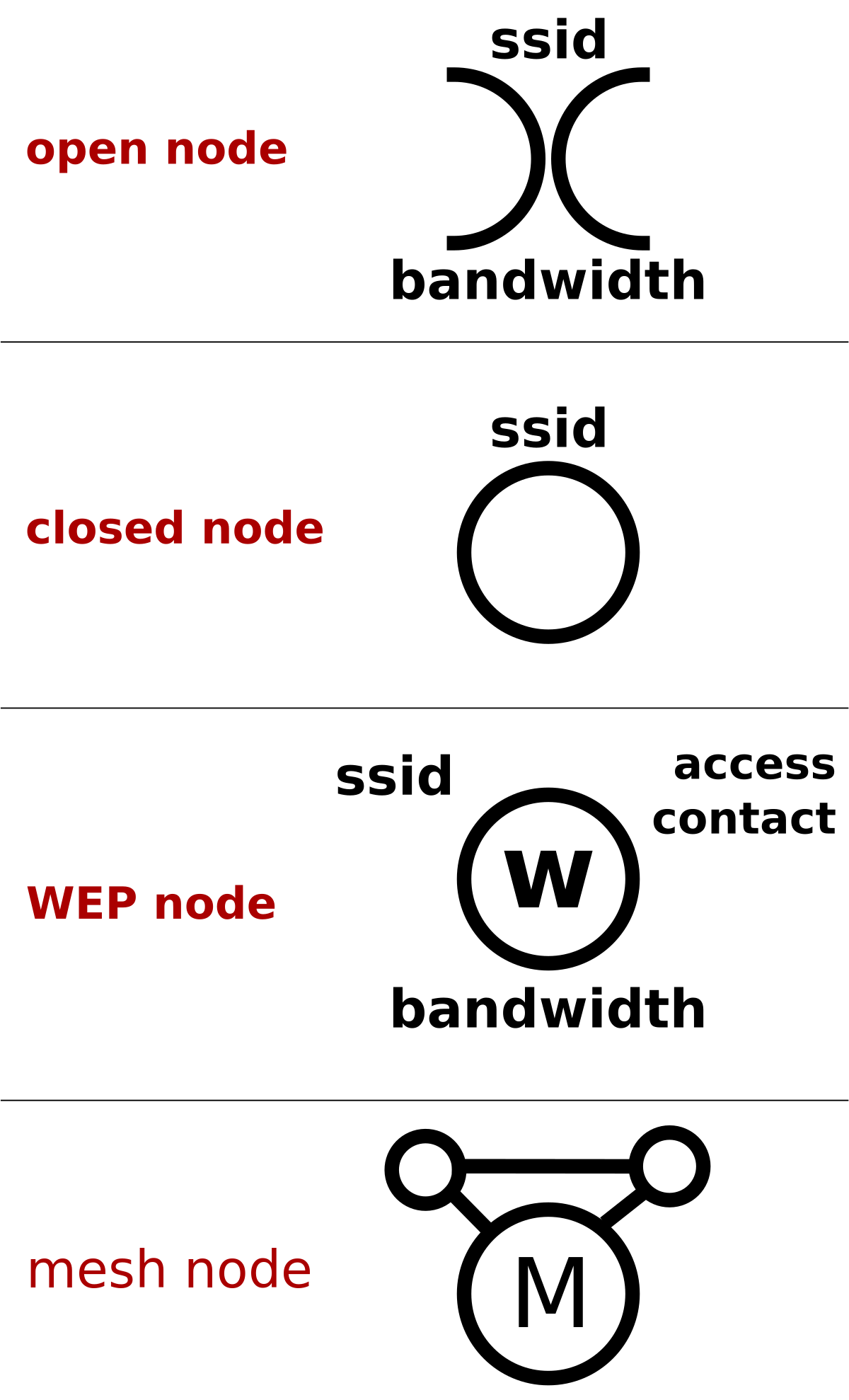
While we are on the topic of War, I thought I would introduce another Attack, War Chalking. War Chalking is an area that is physically marked with info about a WiFi signal being present. Yes, this sounds prehistoric, because it is. This method was used from about ’97 to ’02 (hey that was the year before I started High School). Hackers would mark a closed circle to indicate a closed/secured WiFi network, and to back-to-back half circles would stand for an open network. Obvi, this is not necessary anymore, since all we need to do to find a WiFi signal is check our mobile phones.
Next up, Replay Attacks. Replay attacks mainly focus on the abuse of authentication at initial setup. When a new connection request comes in, client server, the Hacker will capture the request and then replay that connection by fooling the server and making it believe that it is a kosher connection. Lol, its like dating. You meet someone new and you think he’s the man, but then later on you learn that he provided false pretenses at initial authentication.